Users Play A Critical Role In Preserving Security

Written By Dennis Webb:
The internet has made it extremely easy to quickly obtain and transfer information. While global connectivity is very convenient, it also increases an organization’s vulnerability to outside attacks. The primary goal of an organization’s Information Security program is to protect their information and information systems from unauthorized access and ensure systems are available to its users.
Organizations make a financial investment and work extremely hard to ensure that proper security technologies are implemented, configured correctly, monitored efficiently, and properly maintained. Other processes are established regarding the proper use and protection of the information systems and data, such as Security Awareness Programs, security policies and acceptable use standards.
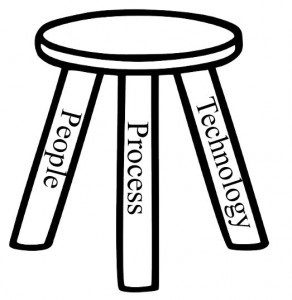
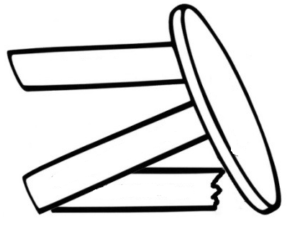
Information Security is like a three-legged stool made up of Technology, Process, and People. If any of the three legs breaks, so does the entire organization’s security protection. Where is the weakest leg of the stool? The people authorized to use the systems and data. Phishing and social engineering are two techniques that are responsible for vast majority of security incidents within an organization.
Every individual has a responsibility to contribute to the overall security of an organization’s information systems and the confidentiality of the data environments. It is essential that authorized users abide by the principles outlined in your organization’s Information Security program to protect themselves and the organization’s systems that they access.
Understanding your responsibilities for protecting systems and stored data and how you can assist in preventing attacks contributes significantly to the overall safety of your organization’s systems. This knowledge usually comes from an organization’s Security Awareness program and can be supplemented by independent awareness of possible attack methods, especially those that are user-focused.
Social engineering relies on human nature to be successful. Searching for weaknesses in the deployed security technologies can take considerable time. Instead, hackers attempt to trick individuals into revealing passwords and other information such as login IDs, server names, operating systems or other sensitive data. A user doing so can lead to compromising an organization’s security. This social engineering can be done via email, telephone or in-person, with the first two being the most prevalent. For example, a hacker may attempt to gain system information by posing as a service technician or system administrator with an urgent access problem.
With every individual playing a vital role in preventing social engineering attacks, understanding social engineering behaviors enables you as an authorized user to recognize them and avoid providing important security information to unauthorized sources. Verifying the identity of the requesting party, never giving out passwords, not providing employee information, not following commands from unverified sources, and not participating in telephone surveys are steps individuals can follow to respond to potential social engineering attacks.
Phishing is another well-known social engineering scam that every authorized user should be aware. Phishing uses emails or websites to deceive users into disclosing sensitive information, such as passwords, credit card numbers, bank account information, and email addresses. Phishers often pose as your internet service provider, bank, online payment service, government agency, or even an executive of your organization. Typically, this is done in an email stating that you must update or validate your account information. It directs you to a website that looks just like the legitimate organization’s site. The email may even threaten some dire consequence if you don’t respond. The purpose of the bogus site is to trick you into divulging your personal information allowing the hackers to exploit your identity or install malicious code on your system.
If you ever feel that you may have been the target or victim of social engineering, phishing, or any other security attack, it is essential to follow your organization’s procedures for reporting security incidents.
Many more nefarious methods exist that hackers employ to gain access to an organization’s protected systems and data. Social engineering and phishing are just two examples used here to highlight the role a user plays in protecting an organization’s systems and data. By making skepticism a part of your normal behavior, as well as practicing a level of security common sense, you will be fulfilling your responsibility as an authorized user on your organization’s systems.
 Dennis Webb – Consultant
Dennis Webb – Consultant
Dennis has over 33 years of progressive Information Technology and management experience. He is recognized for his ability to work with executive management and technology experts to translate business goals into effective IT strategies and architectures. He is particularly effective in seeing strategies implemented through project planning and management, team leadership, client communications, and hands-on technical work.
 Tap to email
Tap to email
